Visa clarifies data retention danger
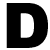 istortion of information isn't restricted to the party game Telephone. It also can happen with news delivered by a deep throat somewhere in the payment processing industry. Such is the case with a warning Visa U.S.A. issued to merchant acquirers last month that put Frisco, Texas-based Fujitsu Transaction Solutions Inc. on the defensive. istortion of information isn't restricted to the party game Telephone. It also can happen with news delivered by a deep throat somewhere in the payment processing industry. Such is the case with a warning Visa U.S.A. issued to merchant acquirers last month that put Frisco, Texas-based Fujitsu Transaction Solutions Inc. on the defensive.
In a statement about the warning, Visa noted that it "provided a confidential alert to a limited number of acquiring members advising that a particular configuration of certain software could result in the storage of sensitive cardholder data.
"The alert also included information regarding the availability of a software upgrade to address the potential for inappropriate data retention."
The twist implying that a flaw in Fujitsu's POS software put customer data at risk came through a third party.
"When Visa's alert came out and they mentioned our software, they did not mean for it to indicate that there was a problem with our software," Ed Soladay, Fujitsu's Chief Operating Officer said.
"It was misleading the way the article [The Wall Street Journal, March 17, 2006] came out. Visa issued another alert that goes into more depth and explains what they were trying to convey.
"I can't comment on the alert other than to say that after discussions, Fujitsu and Visa agreed that it would be better to put out another alert that fully explained what they were trying to say in their original alert, and it had nothing to do with Fujitsu's software at all. Visa was trying to point out that there is a possibility of a security breach of some kind based on people using utilities in the incorrect manner.
"We work very closely with Visa ... Any kind of customer data and everything transported through our software is data encrypted. We are fully in compliance with PCI standards, and all the utilities we provide that go with our software are also PCI compliant."
Problems occur on site when merchants add utilities, unaware that their actions can create vulnerabilities in their systems. "Every software provider today has some type of tracing utility that can be made available to retailers to help them find areas of concern, bugs and things like that," Soladay said.
"We strongly recommend to all of our retailers that if they're going to use any type of tracing utility that they do it in a lab environment only and make sure they delete all data when they're through with it. We don't want any client of ours using these utilities in a live environment. But a retailer can download any kind of utility from the Web, from third parties, or write their own. And they can use it in any manner. We have no involvement in how they use it."
Inappropriate data storage is a big no-no under the Payment Card Industry (PCI) Data Security Standard, which was pioneered by Visa and is endorsed by all major card Association brands.
Merchants that store data beyond the time necessary to process transactions are not in compliance with the standard and are subject to sanctions.
To conclude that inappropriate use of utilities played a role in the recent, alarming breach that compromised the bankcards of hundreds of thousands of people would be rash. That case is under investigation by the FBI. (See "Debit PIN theft: The mystery continues" in this issue of The Green Sheet for an update on the investigation.)
| 


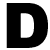 istortion of information isn't restricted to the party game Telephone. It also can happen with news delivered by a deep throat somewhere in the payment processing industry. Such is the case with a warning Visa U.S.A. issued to merchant acquirers last month that put Frisco, Texas-based Fujitsu Transaction Solutions Inc. on the defensive.
istortion of information isn't restricted to the party game Telephone. It also can happen with news delivered by a deep throat somewhere in the payment processing industry. Such is the case with a warning Visa U.S.A. issued to merchant acquirers last month that put Frisco, Texas-based Fujitsu Transaction Solutions Inc. on the defensive.


